Caden Grover
Computer science and cybersecurity student building secure systems and tools to solve real-world problems.
Themes
About Me
Hello, Im Caden, a developer and a cybersecurity student with a strong interest in building practical and useful tools. I have a background in software engineering and spend alot of my time exploring areas like malware analysis, threat detection and secure systems design. Whether im developing a project, looking at network logs or expirementing with Raspberry Pi setups, I enjoy solving complex problems and learning something new along the way.
Lately, ive been interested in projects that combine AI and cybersecurity, along with building reliable systems that are nice to look at and are able to work in real world environments. I care about writing solid code, understanding how things work and continuously learning and improving my skills. My goal is to create a portfolio that reflects the depth of my skills and my creativity, in order to keep growing into someone who can make a real impact in the field.
In my free time, you can find me working on side projects or diving into CTF's, but I also make time for gaming, working out or playing with my cat!
Experience
AI Research Assistant
(AI)² @ George Fox University
July 2025 - Present
- Developed and deployed an automated, LLM-powered SQL query generator using n8n and PostgreSQL, enabling non-technical teams to independently access and analyze financial data.
- Engineered a data integrity solution to prevent the double-counting of transactions by correctly handling duplicate debit and credit entries, ensuring accuracy in financial reporting.
- Wrote and maintained Python scripts to automate new employee onboarding and streamline the collection of user query and response data, improving operational efficiency.
Software Engineer Intern
Tanoshi
Jan 2025 - May 2025
- Automated backup processes and optimized operational workflows using Python scripts.
- Wrote and maintained scripts for testing and streamlined onboarding setups for new employees.
- Contributed to secure software practices and documentation across the development team.
Technology Consultant
Third Wave Psychotherapy
Apr 2023 - Present
- Built and maintained IT systems for operational efficiency and user experience improvements.
- Delivered technical solutions tailored to business needs and compliance standards.
- Analyzed existing business processes and identified areas for improvement or automation.
Lifeguard
Raging Waters
Jun 2020 - Sep 2021
- Ensured guest safety and provided emergency response as part of a 100+ member team.
- Supervised guests in high-traffic aquatic attractions to prevent accidents and ensure compliance with safety rules.
- Maintained current First Aid, AED, and CPR certifications.
Education
B.S. in Computer Science, Cybersecurity Concentration
George Fox University, Newberg
2023 - Present
- - Major in Computer Science
- - Minor in Cybersecurity
- Relevant coursework: Data Structures, Algorithms, Computer Security, Network Security, Ethical Hacking, Architecture and Assembly Language
Projects
Developer Portfolio Website
Designed and deployed a personal portfolio showcasing projects, cybersecurity work, and technical skills. Built with HTML, CSS, and JavaScript featuring a responsive design and smooth animations.

Chess in C++
Implemented a full chess game in C++ with object-oriented design, including game logic, move validation, and basic AI opponent functionality. Demonstrates strong OOP principles and problem-solving skills.
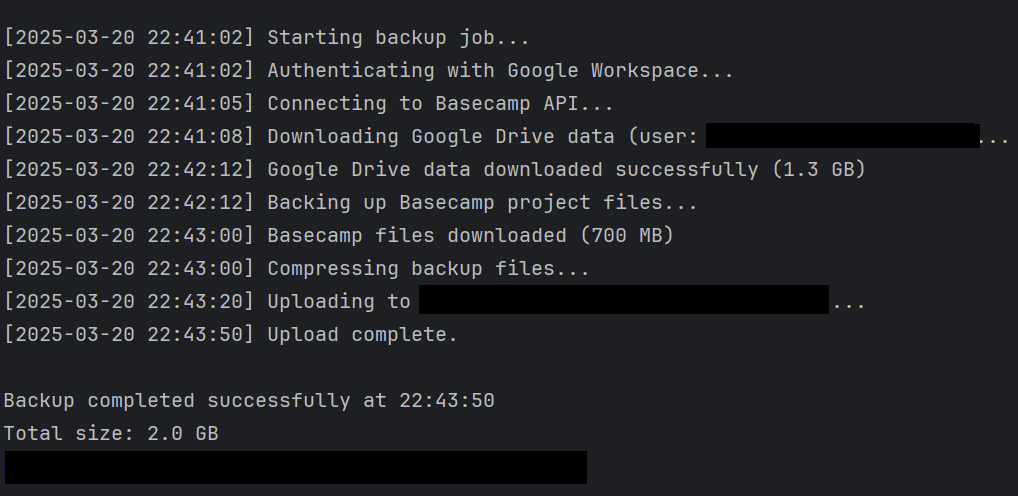
Google Workspace & Basecamp Backup Automation
Built Python scripts to automate secure data backups from Google Workspace and Basecamp, improving data reliability and reducing manual effort in the backup process.
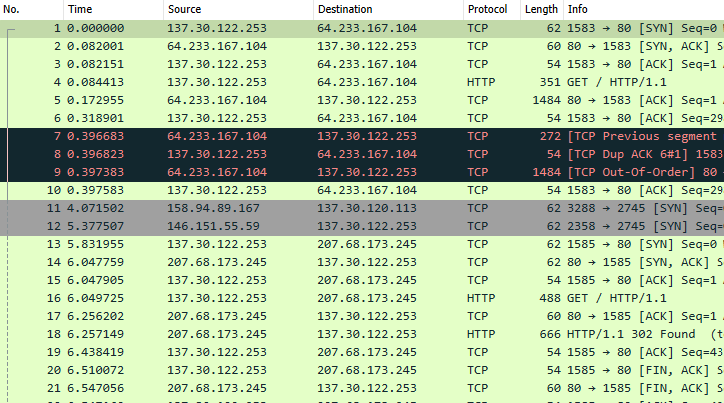
ReconX
Developed a tool in Python using the IntelX API to retrieve, parse, and format intelligence data based on user input, improving data accessibility and analysis for security research.
Achievements
National Cyber League - 2023
Competed in cryptography, network forensics and ethical hacking challenges
CyberSEED - 2025
Placed 23rd out of all U.S. college teams in ethical hacking capture-the-flag challenges
Certifications
- CompTIA Security+ (in progress)
- Verizon Cloud Platform Certification
- MasterCard Cybersecurity Certification